
Der Spiegel’s recent flurry of Snowden documents have been causing somewhat of a paranoid uproar in the etch community. As the various American security services demand that big companies not let the public have access to industry level encryption, we learn that the NSA have the ability to turn vast botnets from hostile hackers to their own purposes.
According to the documents, in 2009 NSA hackers were able to co-opt a botnet as it attacked US Department of Defense systems, turning the vast network of slaved computers into a usable weapon. Tricking the computers into thinking the security service was a command and control server was the name of the game, and once the NSA were in charge, the botnet was swiftly put to use in tracking down its original owner.
SEE ALSO: LMobile Tech Made $3.3 Trillion in 2014
Found to be run by Chinese hackers, the NSA was then able to monitor the situation, and peek over the shoulders of the Chinese hackers as they move on to target United Nations servers and steal documents. What’s worrying here however, is the practice of ‘fourth party collection’, which in this case meant that the documents taken by the Chinese were then acquired by the NSA.
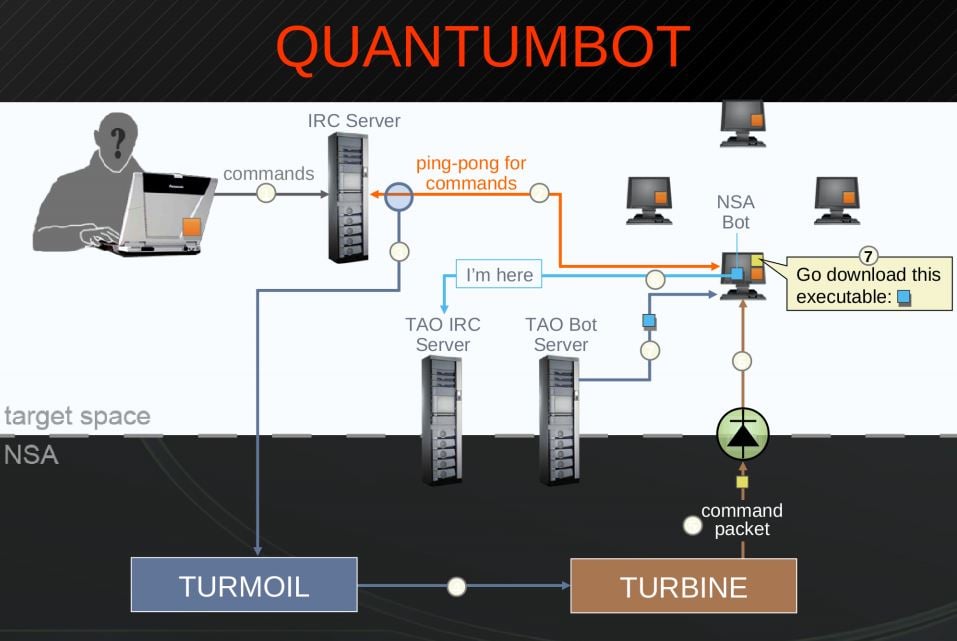
Every time a hacking attack begins, a breadcrumb trail is left back to the origin point of the attack, and in the past few years the NSA has been able to take advantage of this, to intercept information not only from hackers but also the victims. To some, this is a threat – even if the NSA manages to stop hackers, they reap their own rewards by taking control of sensitive data stolen.
It must be said that world security as a whole does benefit from these attacks – source code for Chinese malware and other sensitive information in this case was recovered from the origin point of the 2009 hack. However, when American security agencies have such unprecedented access to documents stolen by hackers they are shadowing, what is to stop them using that information to the detriment to the victim, albeit covertly?
SEE ALSO: Beijing Seeks Tech to Tackle Smog Problem
Botnet piggybacking is also frequently becoming a problem for those in charge of the slaved computer networks, on top of the ability of security agencies to block more primitive forms of attack, such as the protest tool Low Orbit Ion Cannon, relatively easily. What this means is that US interests are able to use computers slaved all over the globe as cannon fodder in their own attacks, without providing compensation to foreign victims of cyberwarfare outside of the US.
More Snowden revelations from the 1.7 million strong cache of information are slowly being released by newspapers and journalists given the information by the whistleblower. The revelations are making it seem more and more obvious that cyberwarfare is becoming the new front line for irresponsible superpowers to launch petty attacks against each other, unwittingly funded the general public.
Via: The Register
Source: Der Spiegel
